Food Defense Mitigation Strategies
Food Defense Mitigation Strategies
Preventing Intentional Adulteration
What are food defense mitigation strategies?
Mitigation strategies are defined by the rule as those risk based, reasonably appropriate measures that a person knowledgeable about food defense would employ to significantly minimize or present significant vulnerabilities identified at actionable process steps. Those measures must also be consistent with the current scientific understanding of food defense at the time of the analysis.
For example, your food defense team has identified a significantly vulnerable step in your process where a mixer is oftentimes left unattended with product inside. A mitigation strategy may be to control access so no unauthorized personnel would be allowed to access the mixer during vulnerable times.
Are mitigation strategies required?
What are the requirements?
As stated above, for each identified actionable process step in your process, you must identify and implement mitigation strategies in order to significantly minimize the risk for intentional adulteration of your products. Remember, an inside attacker is likely your biggest threat. Also, for each mitigation strategy implemented, the facility must also provide an explanation of how the mitigation strategy prevents or significantly reduces the vulnerability associated with the actionable process step.
For instance, in the example given earlier where controlling access to an unattended mixer has been identified as a mitigation strategy at this actionable process step, an explanation of why the mitigation strategy was chosen might look like the following:
Access to the mixer will be controlled by closing and securing the lid with a combination padlock where only approved personnel have the code to open the lock. This will prevent unauthorized personnel from accessing the mixer and potentially adding a contaminant to the mixer while it is left unattended.
Both the strategies and explanations that are developed must be written and directly relate to the significant risk that was identified during the vulnerability assessment.
The Mitigation Strategies Database
A helpful tool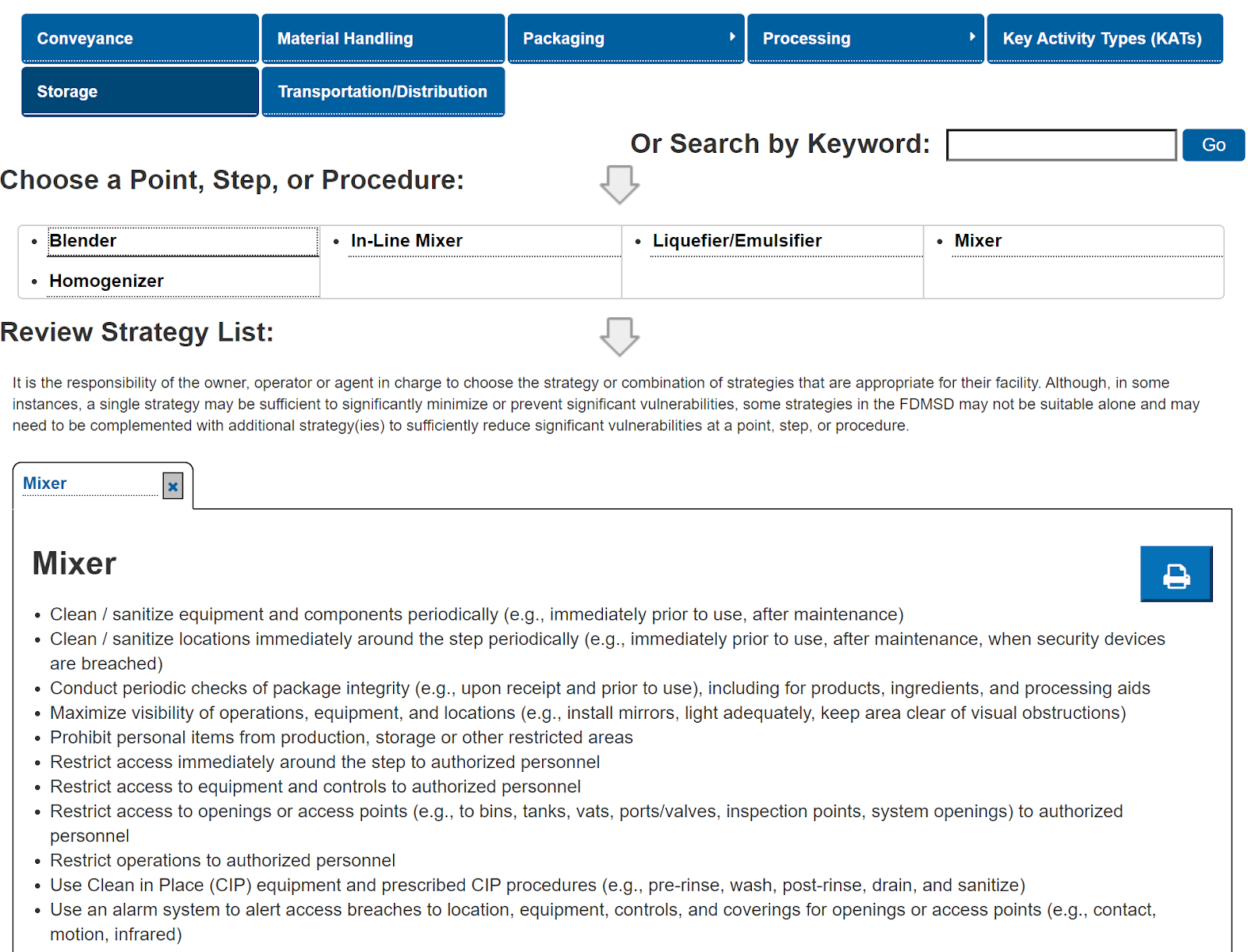
Management Components
1. Food defense monitoring
2. Food defense corrective actions
3. Food defense verification
C. Contaminant-specific analysis
Summary
About the author

Lance Roberie
Food Safety Consultant and TrainerLance Roberie has over 20 years of quality assurance and food safety experience within the food industry. Mr. Roberie holds the following certifications:
- Certified Food Safety HACCP Manager
- Preventative Controls for Human Foods (PCQI) Lead Instructor
- Meat & Poultry and Seafood HACCP Lead Instructor
- FSPCA Food Defense (IAVA) Lead Instructor
- ASQ Certified Manager of Quality & Organizational Excellence
- ServSafe Instructor and Exam Proctor
- Internal Auditor and GFSI Specialist
Lance and the Food Safety & Quality Services’ training curriculum will advance your team's food safety knowledge through certified training, consulting, and “real life” industry scenarios.
upcoming Classes
June 13, 2024 09:00 AM - 04:00 PM
June 11, 2024 08:00 AM - June 12, 2024 04:00 PM
June 18, 2024 08:00 AM - June 19, 2024 04:00 PM
Need a Food Safety Specialist?
Free 15 Minute Consultation.Learn how we helped Abita Brewing Company pass their first food safety audit with an A grade.

